Overview
This report is the analysis of a Remote Access Tool (RAT) which is usually named PlugX (also known as Gulpix, Korplug). This malware is often used in targeted attacks against private organizations, governments, political organization and even some individuals. This PlugX variant is interesting on several aspects like the use of a perfectly valid signed binary in order to perform its attack. It also features mechanisms in order to defeat protection like Windows UAC (User Account Control). The purpose of the analysis is to improve the detection at the potential victims site but review the security measures in place within other organization to limit the impact of such targeted attack.
Report
- Complete PlugX analysis report in PDF format (version 1, March 28 2013)
- Loader (in C) to start and launch the PlugX encrypted payload for debugging (version 1, January 17 2014)
Recommendation
-
CIRCL recommends private organization or any potential targets to verify the Indicator of Compromise (IOC) contained in the report (appendix A) to detect any potential infection. CIRCL can be contacted in case of detection.
-
CIRCL recommends to review the infection process of PlugX in order to assess the security measures taken into an organization.
Overview of the PlugX infection process
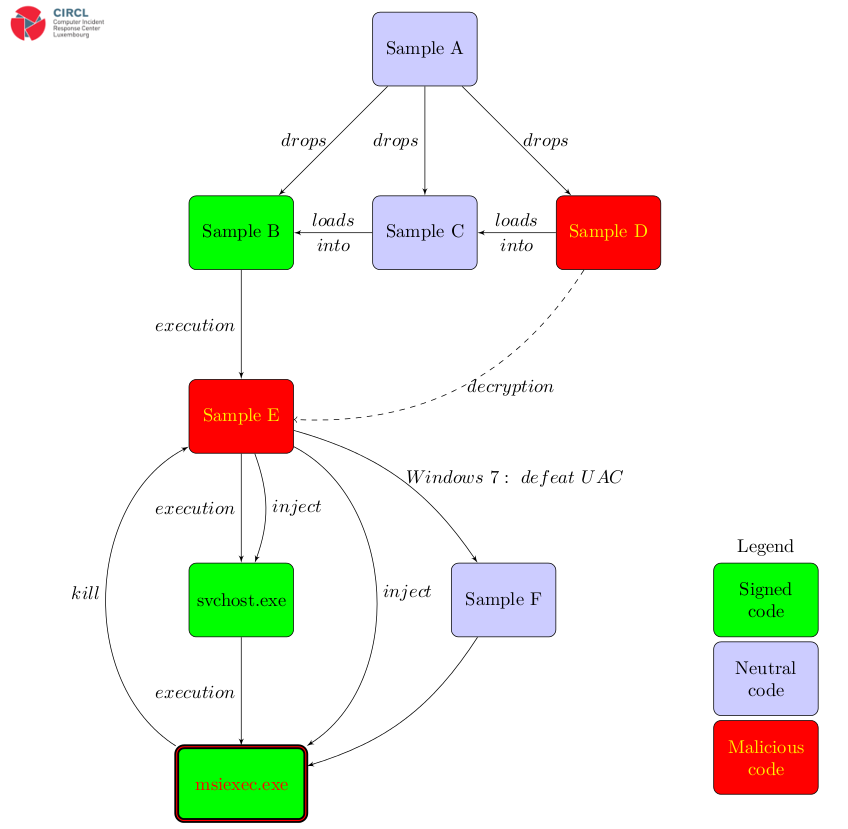
The infection process is fully described in the PlugX analysis report.
Classification Of This Document
TLP:WHITE information may be distributed without restriction, subject to copyright controls.
Revision
- Version 1.1 January 17, 2014 - Loader added
- Version 1.0 March 28, 2013


