Introduction
In order to protect infrastructure, applying preventive measures, taking appropriate security decisions and/or security measurements are critical aspects.
- Are specific threats or risks a reality?
- Based on the security measures, what should an organisation focus on or prioritize on?
CIRCLs goal is to gather objective and repeatable metrics to support the decision process in security at large. As CIRCL operates various tools (such as honeypots, black-hole monitoring, information sharing tools or active monitoring tools), we provide an automated overview of the collected information and their potential support to make a decision. This page is automatically updated to provide a basic situational awareness overview based on measured information. Topic will regularly follow new sources of information which can be measured efficiently.
Topic: IoT security
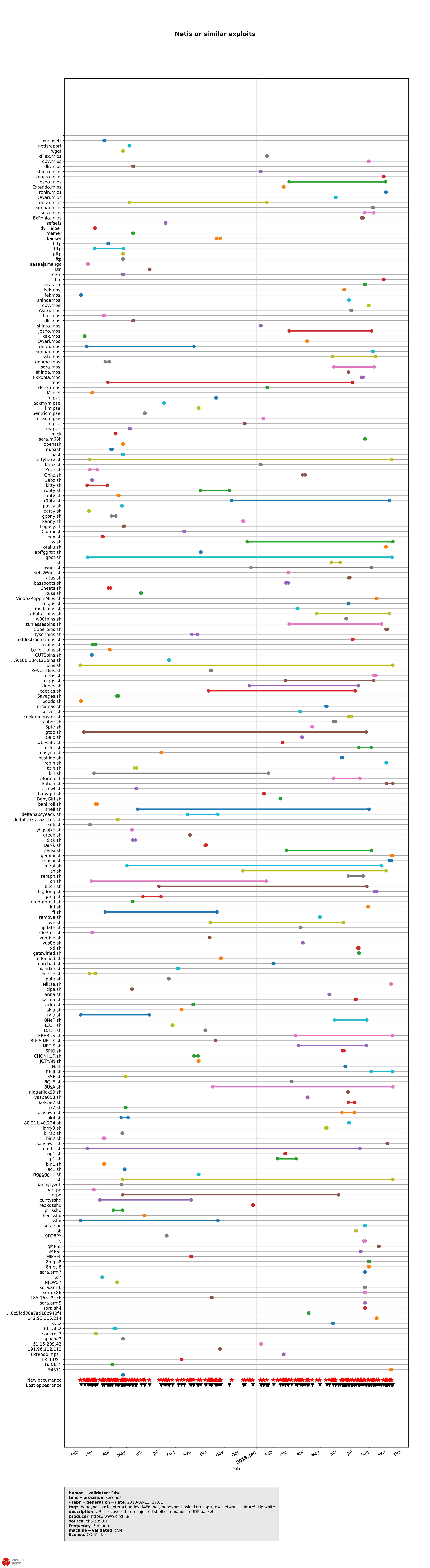
IoT security is an often mentioned topic, but it remains very challenging for an organisation to perceive the real risk associated with IoT devices. The metrics below show the persistence of adversaries against specific vulnerable IoT devices, showing their dedication and regular activities targeting devices.
- Recommendations
- Filtering (before connecting) IoT devices is a MUST following the persistence of attackers to reach vulnerable equipments
- Reviewing equipments and devices which can be considered as IoT and ensure software updates
Observed abuse using UDP packets with shell escaped payload
URL lifetime in shell escaped payload
URL activity in shell escaped payload
Topic: Human errors
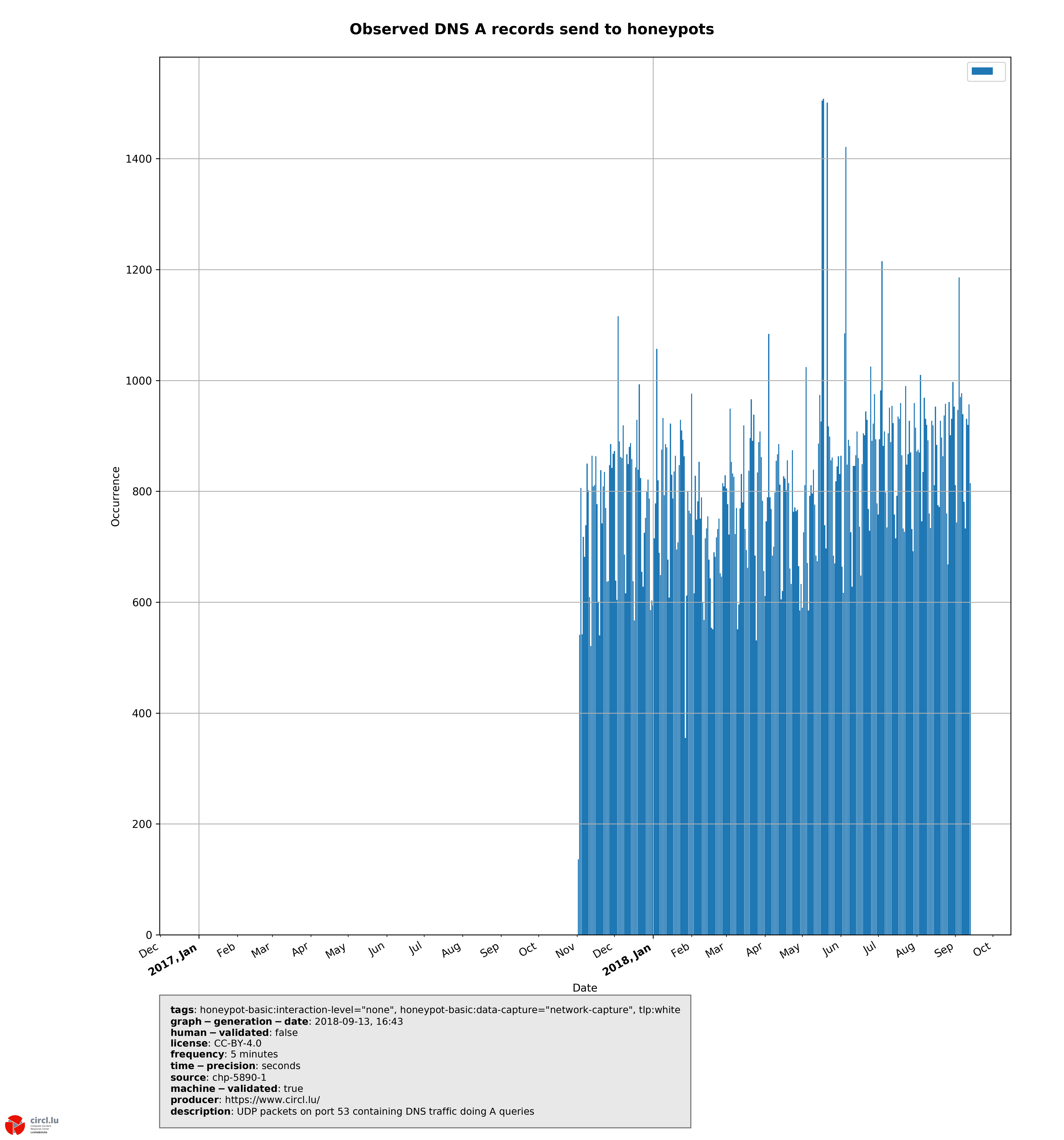
Human errors are often difficult to measure. In the case of our honeypot network, CIRCL collects misconfigured DNS queries leaking to honeypots. The DNS queries shown a business day pattern which demonstrates the misconfiguration aspect of the DNS in corporate environments.
- Recommendations
- Ensure correctness of your DNS configuration
- Disable recursive DNS queries for internal systems
DNS queries (A) received by honeypot
Classification of this document
TLP:WHITE information may be distributed without restrictions. The document and the Open Data mentioned are licensed under an international CC-BY 4.0.
The document including graphics and diagrams can be freely reused following the international CC-BY 4.0.
References
Revision
- Version 1.0 September 13th, 2018 Initial version TLP:WHITE.