CIRCL - Coordinated Vulnerability Disclosure (CVD) Policy
CIRCL, in its role as a Computer Security Incident Response Team (CSIRT) under the NIS 2 Directive, receives reports concerning vulnerabilities in ICT products, ICT services, or processes, or discovers such vulnerabilities through its own activities. This Coordinated Vulnerability Disclosure (CVD) policy outlines the structured process CIRCL follows, acting as a trusted intermediary to facilitate interaction between the reporting entity/individual and the manufacturer or provider of the affected ICT product or service (‘the entity concerned’).
This policy adheres to the principles outlined in Article 12 of the NIS 2 Directive.
Its primary objectives are:
- To identify and contact the concerned entities;
- To provide assistance to natural or legal persons reporting a vulnerability;
- To negotiate disclosure timelines and manage vulnerabilities affecting multiple entities;
- To ensure that diligent follow-up measures are taken by the entity concerned;
- To facilitate safe and coordinated notification to users and customers once a remedy is available or appropriate mitigation advice can be provided;
- To contribute to the European vulnerability database managed by ENISA.
To disclose a vulnerability, reporters can use the following form: https://vulnerability.circl.lu/disclosure/new/.
Overview
Security vulnerabilities can exist in any hardware, software, service, or procedural implementation (such as misconfiguration, insecure default). Coordinated Vulnerability Disclosure is the process mandated and encouraged by the NIS 2 Directive to manage the discovery and remediation of these vulnerabilities, thereby improving the overall cybersecurity posture. CIRCL plays a facilitation role in this process.
Steps
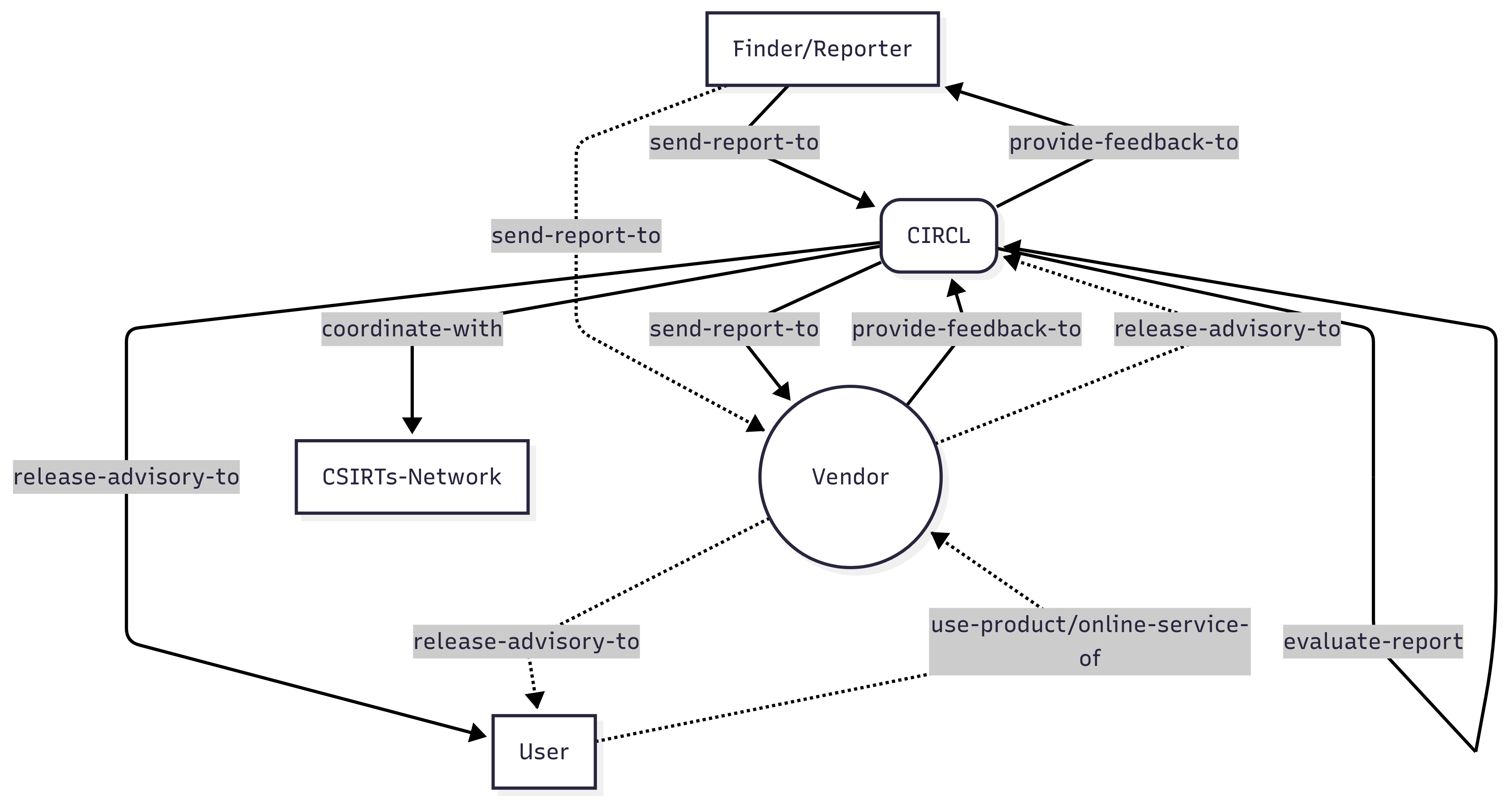
Vulnerability Notification to CIRCL
- Reception: CIRCL can receive vulnerability notifications from named or anonymous natural or legal persons (‘reporters’). Vulnerabilities may also be identified by CIRCL during incident analysis or other activities.
- Reporting Channel: Notifications must be submitted via the official CIRCL reporting channels: https://vulnerability.circl.lu/. An account is required in order to report a vulnerability and ensure the follow-up with the reporter. Disclosure form https://vulnerability.circl.lu/disclosure/new/
- Anonymity: Reporters must clearly state if they wish to remain anonymous throughout the process. By default, and unless anonymity is requested, CIRCL may share the reporter’s identity with the entity concerned to facilitate communication, but only where necessary and appropriate. The disclosure platform allows users to report anonymously by explicitly stating that they wish to remain anonymous.
- Report Quality: CIRCL expects reporters to make a reasonable effort to provide complete and accurate reports, including sufficient technical detail (e.g., affected product/service/version, vulnerability type, potential impact, proof-of-concept/reproduction steps) to allow the entity concerned to assess and validate the finding.
- Guidance: CIRCL will provide guidance to the reporter regarding this CVD process and procedures.
Notification to the Entity Concerned & Coordination
- Validation & Notification: Upon receiving a potentially valid vulnerability report, CIRCL (acting as coordinator) will notify the entity concerned via known secure contact channels if available. If the reporter initiated contact with the entity, CIRCL may be notified by either party to assist in coordination.
- Default Remediation Deadline: The default timeline for the entity concerned to develop and make available a remedy (patch, update, mitigation) is [60] calendar days from the initial notification.
- Timeline Negotiation & Extensions: If the entity concerned cannot provide a remedy within the default period, it must promptly inform CIRCL, providing a clear justification and a proposed remediation plan with an alternative timeline. CIRCL will assess the justification in consultation with the reporter (if not anonymous and willing). CIRCL will mediate discussions to reach a mutually agreed-upon, reasonable extension. Factors considered include vulnerability complexity, impact, and the entity’s responsiveness and remediation efforts.
- ID Assignment: If the vulnerability requires an identifier and the entity concerned is not a CVE Numbering Authority (CNA) or does not have an established process, CIRCL will assign an ID such as a CVE ID but not limited.
Remediation and Coordinated Publication
- Vendor Remediation: Ideally, the entity concerned develops a remedy and coordinates the timing and content of a public disclosure announcement with CIRCL and the reporter. Publication typically occurs once the remedy is available to affected users.
- Publication Content: The publication(s) may include details of the vulnerability, affected products/services, the remedy or mitigation advice, and appropriate acknowledgements (crediting the reporter unless anonymity was requested). Complementary analysis by CIRCL can be published in conjunction with the vendor’s publication.
Handling Non-Compliance or Disagreement
- Mediation: If disagreements arise regarding the vulnerability’s existence, severity, or disclosure timeline, CIRCL will act as a mediator between the reporter and the entity concerned.
-
Disclosure by CIRCL or the Reporter: If the agreed-upon deadline (including extensions) expires, and the entity concerned has failed to provide a remedy or respond adequately, or refuses coordination unreasonably, CIRCL, potentially in coordination with the reporter:
- Will first assess the potential risk to users and the public associated with disclosing the vulnerability information without a readily available remedy.
- May then proceed with publishing vulnerability details to inform affected parties and enable them to take protective measures. This is a measure of last resort. The scope of information disclosed will be carefully considered based on the risk assessment.
- To maintain a coherent disclosure timeline, if CIRCL receives multiple reports for the same vulnerability, it will acknowledge valid submissions but consolidate the coordination. Communication with the entity concerned regarding remediation and the disclosure schedule will proceed as a single unified effort, preventing conflicting timelines.
Cooperation and Information Exchange
- CIRCL collaborates with other national CSIRTs within the CSIRTs Network and with ENISA on vulnerability disclosure practices and specific cross-border cases, as appropriate and in line with NIS 2 requirements.
- Based on risk assessment, CIRCL collaborates with other CSIRTs or PSIRTs to coordinate the disclosure process, including any necessary pre-notifications, for reported vulnerabilities.
Reporter Considerations
- Reporters must ensure their vulnerability discovery activities comply with applicable laws in the Grand-Duchy of Luxembourg.
References
- Directive (EU) 2022/2555 of the European Parliament and of the Council of 14 December 2022 on measures for a high common level of cybersecurity across the Union, amending Regulation (EU) No 910/2014 and Directive (EU) 2018/1972, and repealing Directive (EU) 2016/1148 (NIS 2 Directive) (Text with EEA relevance)
- Vulnerability lookup taxonomies
- Responsible Vulnerability Disclosure Process
- GCVE-BCP-02 - Practical Guide to Vulnerability Handling and Disclosure
Revision
- version 1.0 - 26th March 2025 - TLP:CLEAR
- version 1.1 - 10th April 2025 - TLP:CLEAR
- version 1.2 - 10th April 2025 - TLP:CLEAR
- version 1.3 - 18th June 2025 - TLP:CLEAR


